Securing the Cloud:A Closer Look at AWS IAM in Action
AWS Decoded, Your Ultimate Handbook for Cloud Mastery, Part-2.
About Me:
Hey Folks! Am Vishwa, DevOps and OpenSource Enthusiast. Currently am doing LearnInPublic and BuildInPublic where I'll be documenting my entire journey on LinkedIn and Twitter to be accountable and to connect with many like-minded people to seek knowledge from them and help each other. Here, In this series, I'll delve deeper into Cloud computing, with a specific focus on AWS. This journey enables effortless learning and experimentation. My goal is to simplify complex concepts for all. Let's get into Part 2 of the series which is all about AWS Identity Access Management Service.
What is IAM?
- IAM is a service provided by AWS that stands for Identity Access Management.
- Designed to assist you in managing secure access to AWS resources.
- We can define which individuals or entities are granted access to AWS services and resources.
What problem does it solve?
- It is used to solve problems like Authentication and Authorization.
- Authentication is nothing but who is entering into AWS.
i.e.) Logging into the AWS.
- Authorization means accessing the services or resources in AWS.
i.e.) What or which services or resources one can access?
How does it work?
- The person who has the Admin access will create IAM users.
- The administrator assigns fundamental permissions to individuals based on their roles and the tasks they are intended to perform.
- We can simply say that this service is used as a shared access to the AWS account.
Why it is used?
1. IAM User:
- It is used for Creating a user, which is called an IAM User.
2. IAM Policies:
- It is nothing but What he/she can do with AWS services or the resources.
Example: Imagine you run a social media platform, and you have different roles like "Moderator" and "Content Creator." IAM policies are like rule sets for each role. For example, the "Moderator" policy might allow the ability to review and remove inappropriate content, while the "Content Creator" policy permits posting new content. IAM policies define what actions each role can take and on which resources. So, the "Moderator" policy ensures moderators can moderate content but not necessarily create new posts. Policies help control and limit the actions users can perform, ensuring a secure and well-defined access structure within your platform.
3. IAM Groups:
- A predefined set of policies assigned to an IAM User can be replicated by creating a group with those policies. Subsequently, individuals seeking similar access can be added to that group.
Example: Imagine you have an online shopping platform. In your business, you have different teams like "Customer Support," "IT," and "Marketing." IAM groups act like these teams. For instance, you create an "IT Team" group and assign all IT staff to it. Now, instead of setting individual access for each IT employee, you grant permissions to the "IT Team" group. So, if someone new joins the IT department, you add them to the "IT Team" group, and they instantly get the access needed for their role like managing servers or troubleshooting technical issues. IAM groups simplify managing access by grouping users based on their roles, making it efficient and organized.
4. IAM Roles:
- It shares similarities with IAM users, but it is specifically designed for temporary use, featuring a combination of a username and password for access.
- Roles are used when we want to access services from outside the AWS.
Example: Imagine you work for a company with different departments like HR, Finance, and IT. IAM (Identity and Access Management) roles are like job titles or roles within the company. For example, an "HR Manager" role might have access to employee records, while a "Financial Analyst" role could access financial data. These roles ensure that each employee has the right level of access to the resources they need for their job, without unnecessary permissions. IAM roles help maintain security and ensure that employees only have the access they require to do their work.
AWS Management Console:
- To assist users in managing and accessing their AWS resources, Amazon Web Services (AWS) offers a web-based interface called the AWS Management Console. Users may configure, monitor, and manage their cloud-based infrastructure with it, and it acts as a common center for interfacing with numerous AWS services.
- Let's go through the exact process of creating an IAM user through the AWS Management Console step by step.
Steps for Creating an IAM User:
1. Open your AWS Management Console, find the IAM service using the search bar, and click on it. For easier access, you could see IAM on the Recently Visited list if you've recently interacted with it.
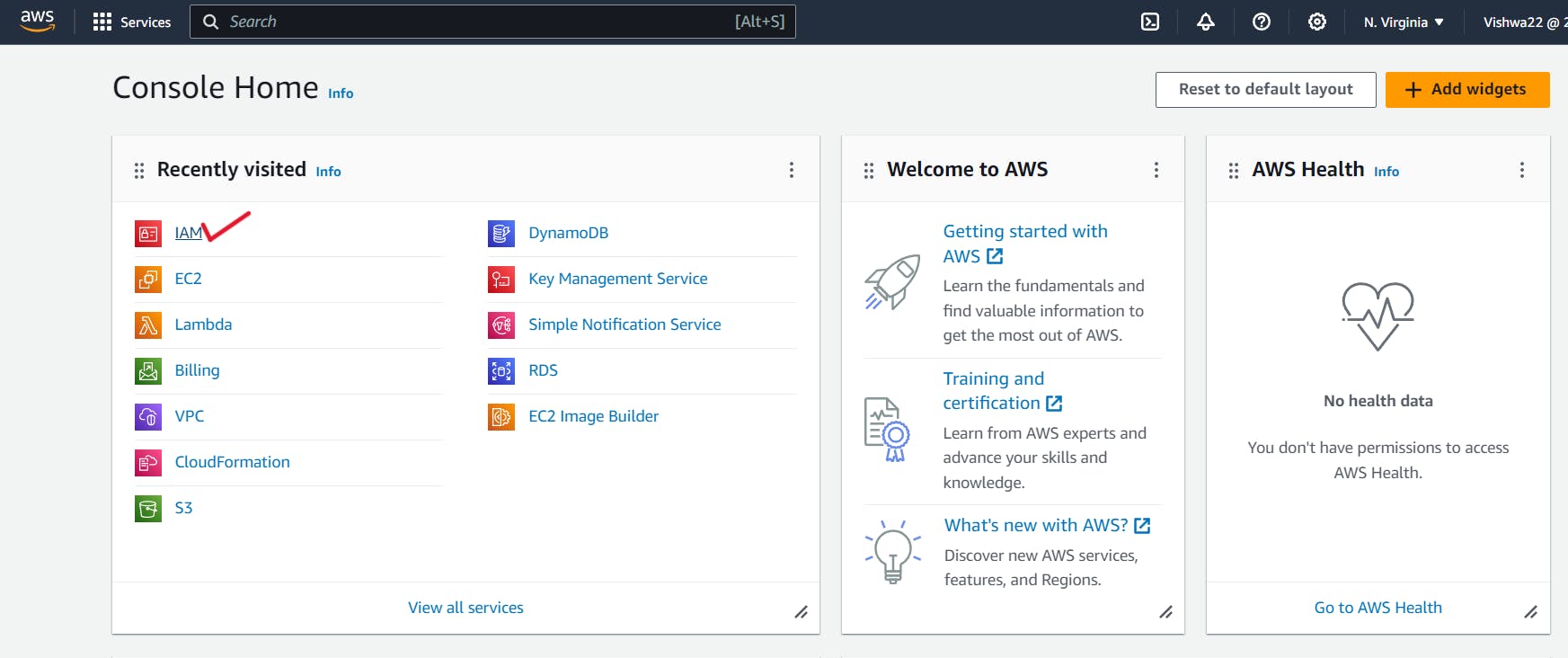
2. After the Dashboard opens, select Users from the Access Management menu.
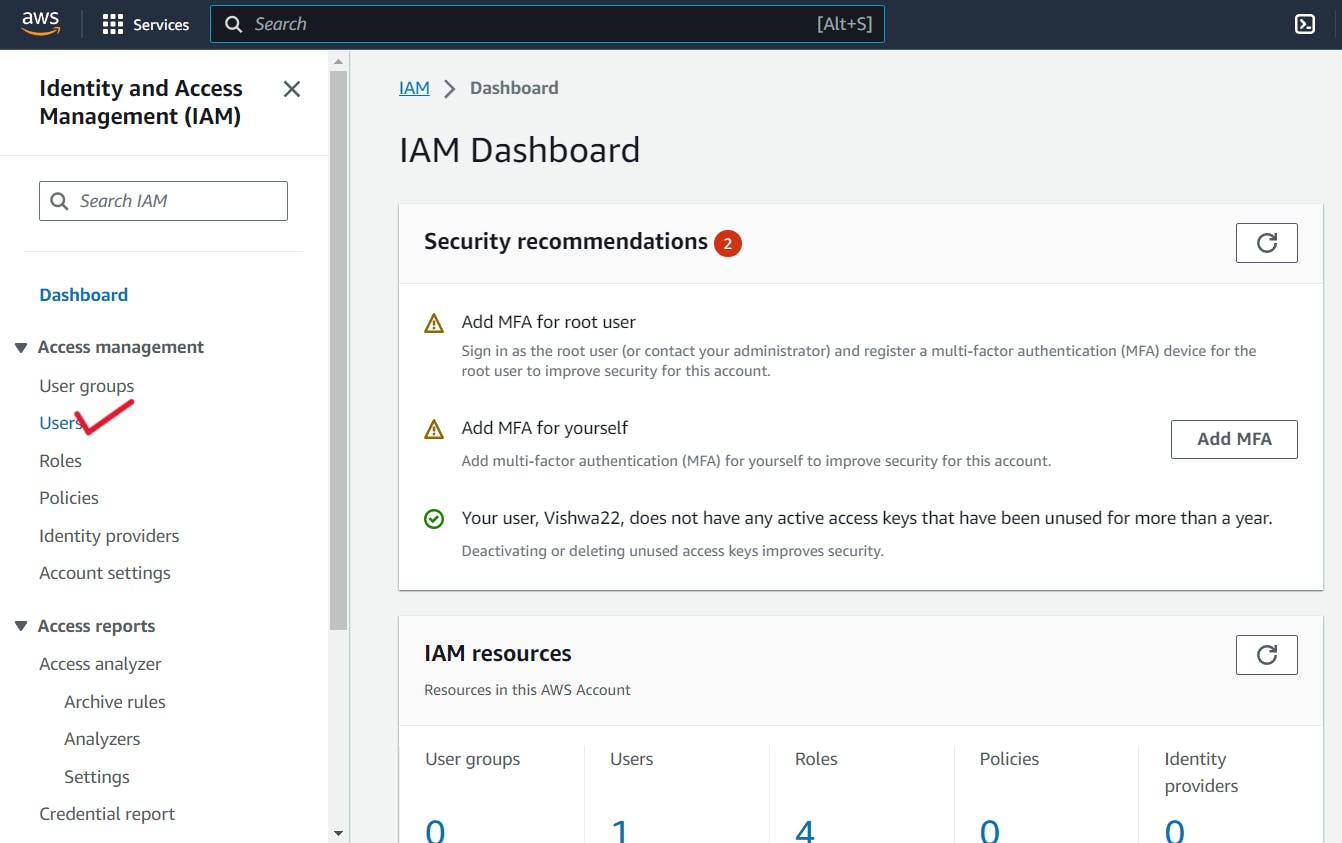
3. You will see a "Create User" option on the screen after choosing the Users option.

4. You can set the user details on the screen that appears after selecting the "Create user" option. Here, the steps are simple to follow.
- Give the IAM user you just created a name.
- Check the box to grant AWS Management Console access to your newly created IAM user.
- Next, choose the "I want to create an IAM user" option.

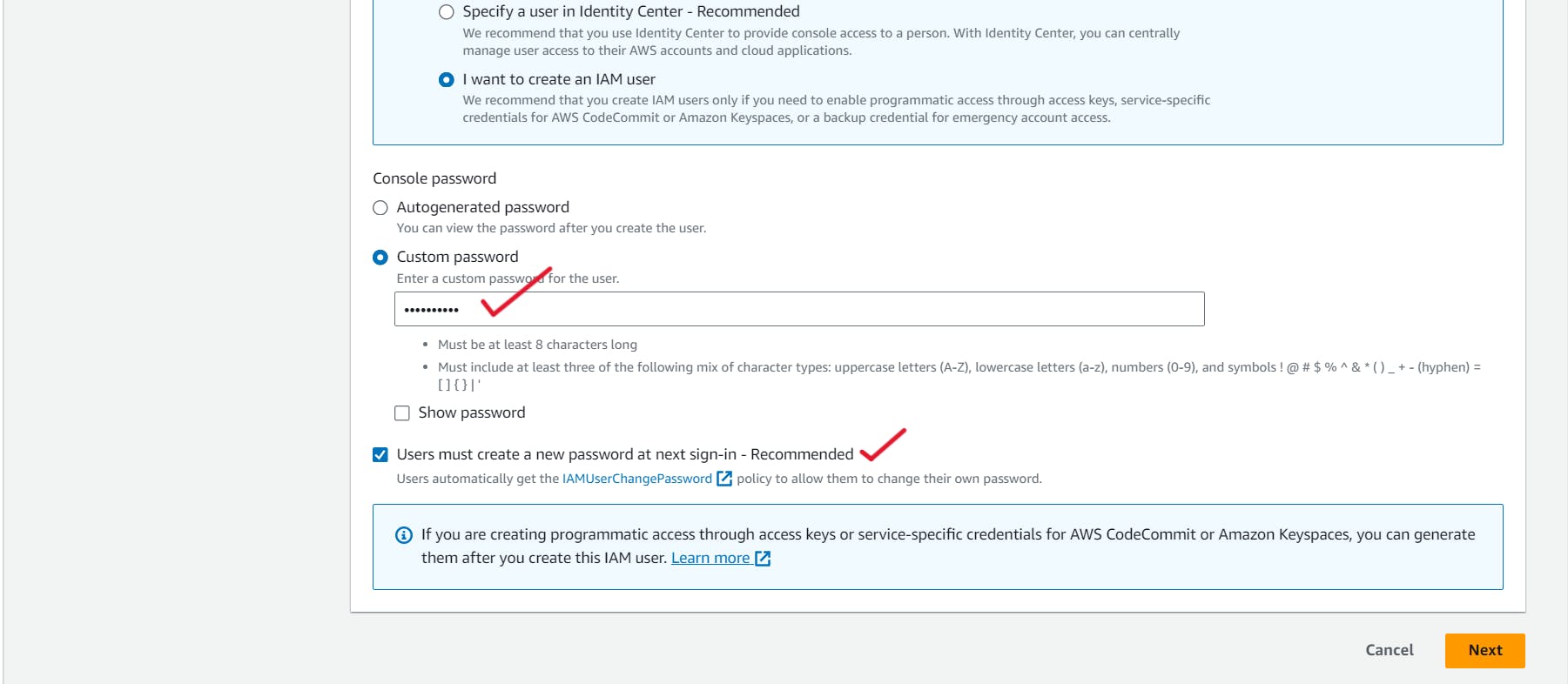
You will be asked to create a new password after it's finished. You have two choices to choose from here, and they are:
- Make an automatic password.
- Establish a unique password.Also, as a recommended practice, you can choose to allow password regeneration when you log in again. Once you've adjusted this setting, click "Next."
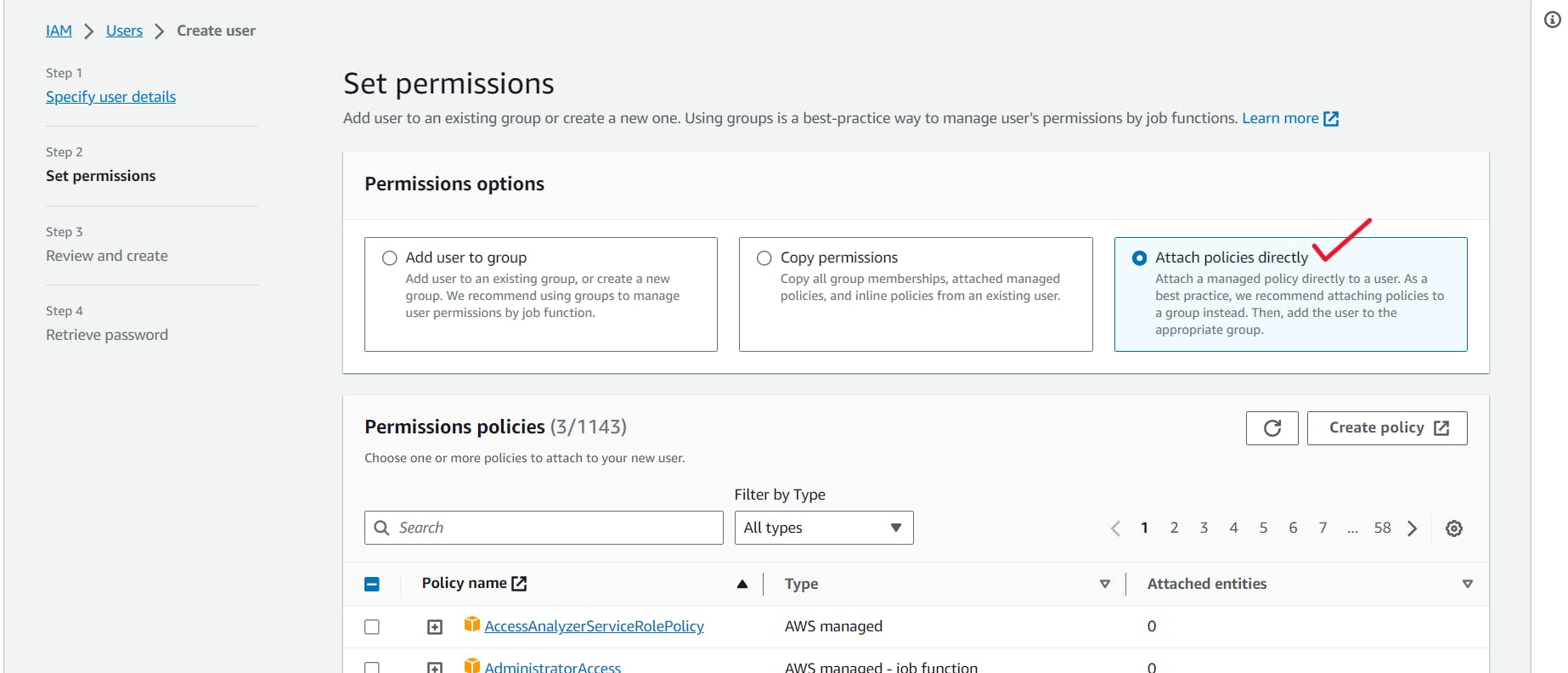
6. Configuring permissions for an IAM user involves several tasks, including:
- Adding this user to a Group,
- Copying an existing permissions to this user,
- Attach policies directly.
A direct policy attachment to the IAM user is the best course of action. Choose this and list the resources and services that the new IAM user will be able to access.
7. After reviewing the user details and permissions summary, proceed to create the user by clicking the "Create User" option located at the bottom right corner of the screen.
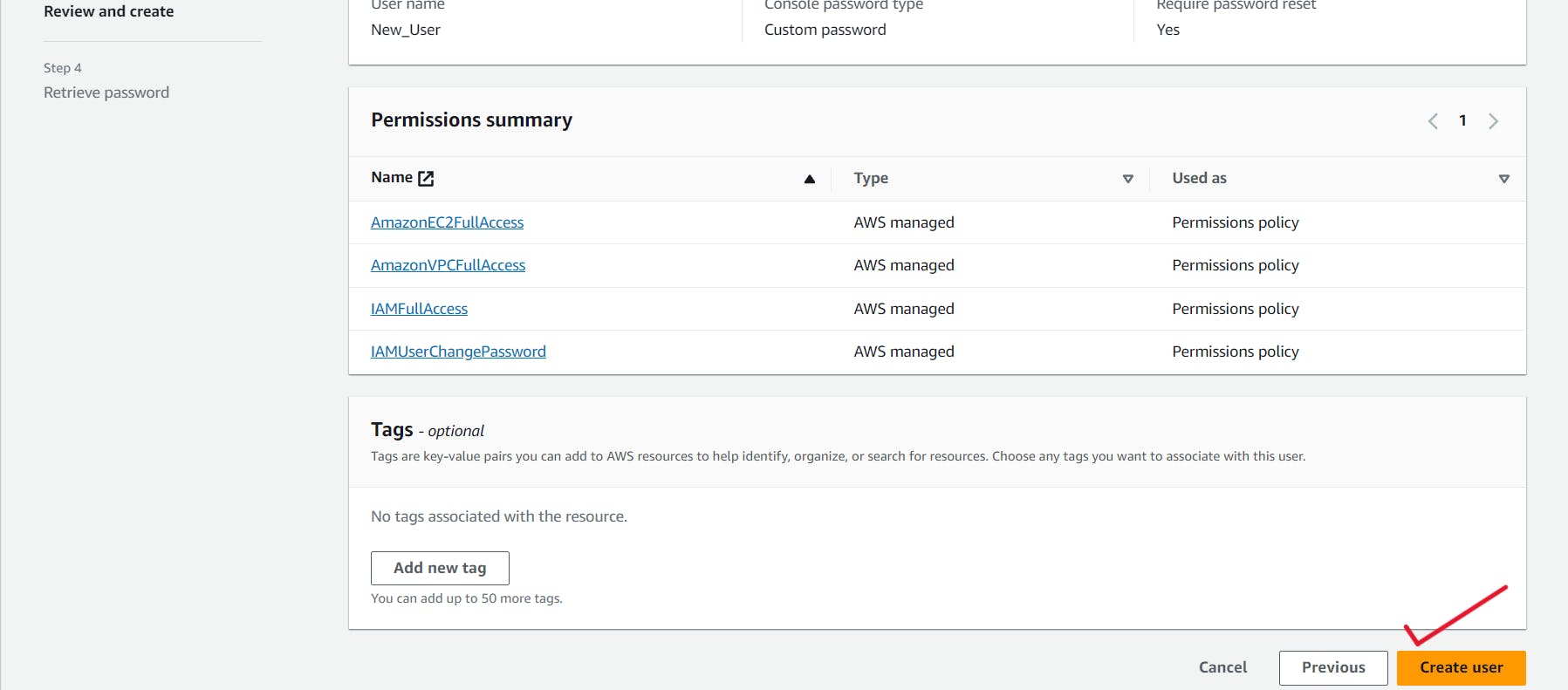
8. A pop-up notification will confirm the new user's addition after it has been successfully created. If necessary, you can download the login credentials or go back to the user list.
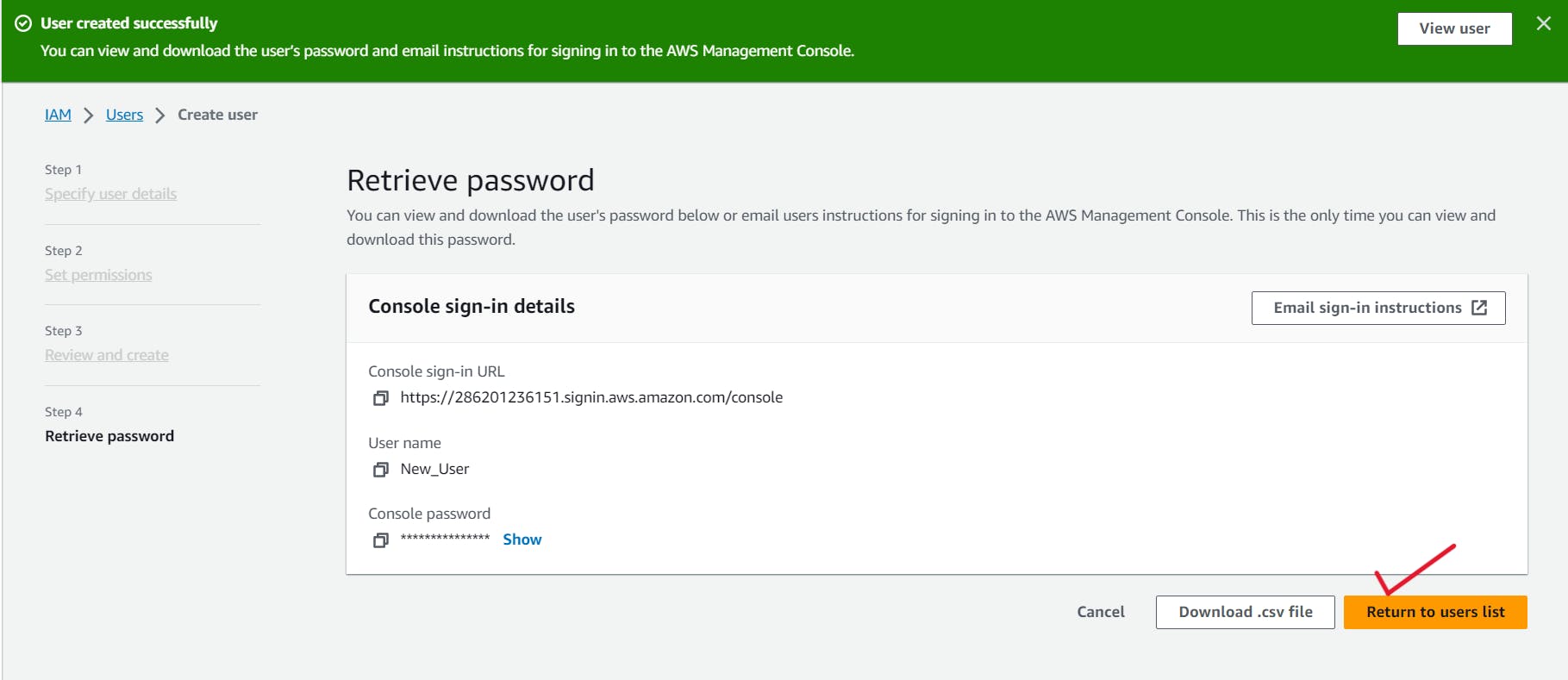
9. Kudos! You have successfully created an IAM user. Proceed to log in using the credentials of the newly created IAM user. Kudos!
In fact, these nine steps give a thorough tutorial for using AWS's IAM service. The IAM service overview and the procedures for creating and configuring an IAM user come to an end here.
Conclusion:
Thank you for your engagement! If you found the information helpful, be sure to hit the like button and share your thoughts in the comment section. Keep checking back for additional articles in the future on AWS and its services, including practical experiences. I value your time and hope to see you in the upcoming post!