Building Secure Networks: AWS VPC Blueprint
AWS Decoded, Your Ultimate Handbook for Cloud Mastery. Part-4.
About Me:
Hey Folks! Am Vishwa, DevOps and OpenSource Enthusiast. Currently am doing LearnInPublic and BuildInPublic where I'll be documenting my entire journey on LinkedIn and Twitter to be accountable and to connect with many like-minded people to seek knowledge from them and help each other. Here, In this series, I'll delve deeper into Cloud computing, with a specific focus on AWS. This journey enables effortless learning and experimentation. My goal is to simplify complex concepts for all. Without any further delay, Let's get into Part 4 of the series that's all about the AWS VPC.
What is VPC?
- VPC stands for Virtual Private Cloud.
- An enclosed private cloud environment within a public cloud is called a virtual private cloud (VPC).
Example: A Virtual Private Cloud (VPC) might be compared to your online neighborhood. Your home is made up of your servers and data, and you want to keep your neighbors that is, the stuff that other people have put online out of your windows. Your VPC protects your online privacy and security by letting you decide who can view what and who can't enter your home. It functions similarly to an invisible fence.
Why do we need it?
- It is used to avoid security breaches.
- Assume it prevents trespassers from reaching your server applications or database.
Example: To build a secure digital space, online enterprises need a Virtual Private Cloud (VPC). Think of it as having your private room in a common building, where you can control and maintain privacy over your online operations while also making sure your data is safe from prying eyes.
Components of VPC:
- Internet Gateway, Public Subnet, Load Balancer, Route Tables, Security Groups.
What is Internet Gateway & Why it is used?
- The function of it is to facilitate communication between the internet and the privately hosted application.
- Consider the Internet Gateway as the front door that connects your house to the internet, the outside world, if your house were a network. Your devices send and receive data through this gateway when they wish to interact with websites or services that are located outside of your house (on the internet).
- Hence, for your computer to load a webpage, it sends a request through the Internet Gateway, which forwards it to the Internet and then transmits the webpage back to your machine.
What is a subnet & Why do we use it?
- Consider subnets like distinct rooms within a VPC. Every room serves a certain function, such as a kitchen for cooking or a bedroom for sleeping. Just as different rooms serve different purposes within a house.
- Similar to how rooms in a house serve different purposes, Subnets help organize and secure digital resources, allowing for efficient management, specific security measures, and independent scalability.
Types of Subnet:
1. Public Subnet: Imagine a public library where people are free to browse the books and resources available. A public subnet is comparable to the reading room of a library in a VPC. Web servers and other resources that require direct communication with the internet are hosted on it. Resources in a public subnet can interact with the internet while upholding a certain level of security, just as patrons of libraries can access books without going into staff-only areas.
2. Private Subnet: Imagine now the staff room of the library, where delicate administrative work is done. This staff room is an example of a private subnet in a VPC. Data that doesn't require direct internet access is stored there, such as databases and application servers. Like the private staff room, only authorized staff can enter, but these resources can securely communicate with each other within the VPC. External access is also prohibited.
What is a Load Balancer and why do we need it?
- It is used to manage the traffic.
- To avoid any one server from becoming overloaded, a load balancer distributes incoming requests evenly, acting as a traffic director for servers. In the same way that a restaurant host controls patron flow to preserve a pleasant dining experience, it guarantees scalability, high availability, and optimized performance.
What is a Route Table?
- A route table in a Virtual Private Cloud (VPC) facilitates effective data routing between several subnets. It guarantees isolation, flexibility, and optimized communication.
Example: Simply put, it directs the flow of data. Similar to how traffic signs direct vehicles to their destinations within a city.
What is Security Group & Why do we need it?
- Security group is used to select which IP to allow and which one to decline.
Example: For your virtual servers, a security group functions similarly to a digital bouncer. It establishes guidelines to determine who is allowed in and who is not. Think of it as a nightclub. The Security Group bouncer verifies if you're on the guest list (approved traffic) and if not, you're not permitted in. Like a bouncer managing venue entrance, it secures your virtual environment by limiting who can interact with your servers and how.
- By using Security Groups, you can make sure that all traffic passes through the ports and protocols you have specified.
NAT Gateway:
- Network Address Translation is used to mask the IP of our server for security purposes. It is used when our application wants to access something from the internet.
Example: A NAT Gateway is like a translator for your private network, imagine NAT Gateway as an office building receptionist. When staff members (private network devices) wish to communicate with clients (the internet), NAT Gateway acts as the receptionist, ensuring that clients see only the office's primary IP address (NAT Gateway) and maintaining the privacy of internal extensions (private IPs). It makes gadgets more secure and allows them to access the internet without disclosing their exact addresses.
Internet Gateway vs NAT Gateway vs Security Group:
- Internet Gateway is for VPC that allows both inbound & outbound traffic rules to communicate with the internet. Similarly, the Security Group is for the applications or servers in subnets. Whereas NAT Gateway changes the original IP for outbound access.
What is NACL?
- Network Access Control List is for allowing inbound and outbound traffic access at the subnet level.
NACL vs Security Group:
- The major difference is at the instance level Security Group only allows the process based on the rules whereas at the subnet level, NACL allows both in & out by creating separate rules for both.
Architecture:
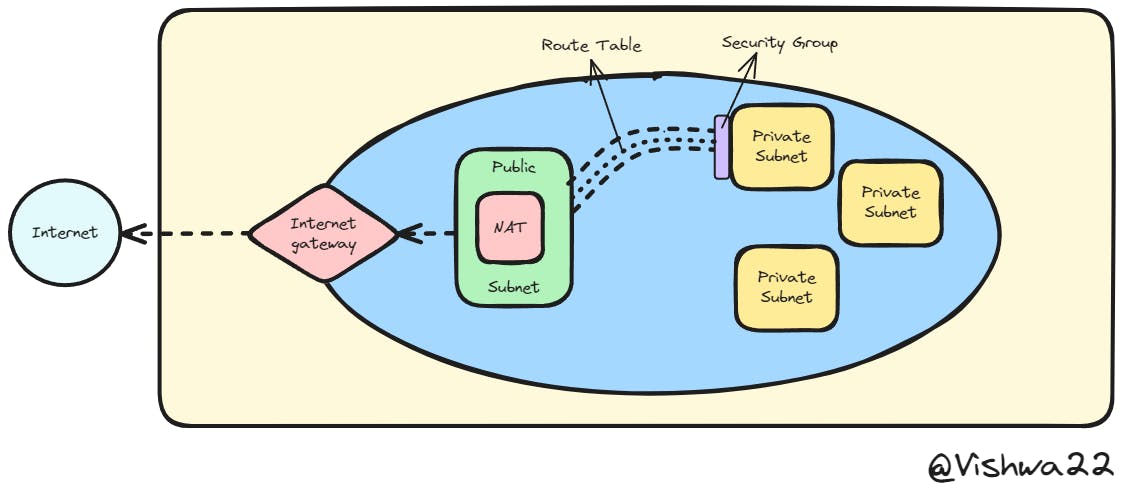
- In AWS, Security is shared responsibility. The Security Group and the NACL is the last point of Security.
Inbound vs Outbound:
- Inbound means allowing access to the resources inside the AWS from the outside world whereas Outbound means applications inside the AWS can access resources in the outside world
Conclusion:
I appreciate everyone who has read it. I hope it was enjoyable for you to read. If you felt it was helpful, please let me know by leaving a comment, like it, and forwarding it to your friends. Next up, let's have a look at AWS S3. Once again, thank you everyone.